ACCELERATED SOLUTIONS
What is Cyber Compliance?
Cyber Compliance is the process of ensuring that an organization adheres to industry regulations, standards, and laws associated with information security and data privacy. Different organizations comply with different cyber security regulations and standards.
- Healthcare organizations - comply with HIPAA regulations that protect patient health information.
- Financial institutions – comply with PCI-DSS regulations that protect credit card data.
- Retailers and e-commerce companies- comply with PCI-DSS regulations if they accept credit card payments online.
- Companies that handle the personal data of European citizens - comply with the General Data Protection Regulation(GDPR).
Cyber Security Compliance Framework
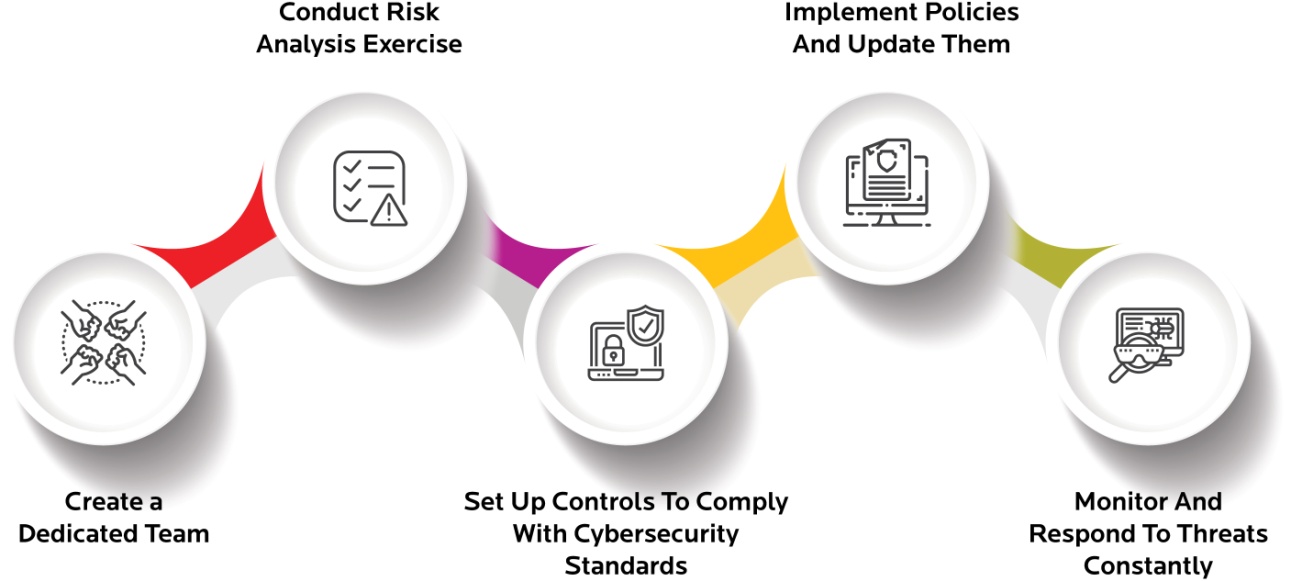
Figure 1
Cyber Compliance Regulations and Government:
Cyber compliance regulation is necessary for government contractors to make sure that defense contractors obtain the cyber security they need to protect valuable information.
Government Contractors nowadays are facing challenges as the Federal Government evolves its business practices to require Cybersecurity throughout the supply chain. Now contractors must make sure that both their own systems and systems of their suppliers are comport with NIST (National Institute of Standards and Technology) requirements. In fact, Department of Defence (DOD) is about to make cyber security compliance a requirement for companies which are performing DOD contracts or subcontracts. As a part of this, DOD is in the process of rolling out the Cybersecurity Maturity Model framework.
The General Services Administration (GSA) is accountable to ensure that contractors remain compliant with the governments cybersecurity policies, which help to make sure the resilience of government systems and networks. To do business with the government, its highly important to understand current Federal Acquisition Regulations (FAR) and other government policies, which defend against compromising sensitive government information.
In recent years, many federal agencies including the Department of Defense (DoD) have issued acquisition regulations that impose new cybersecurity requirements on contractors.
The top four requirements that an organization should be familiar with are listed below:
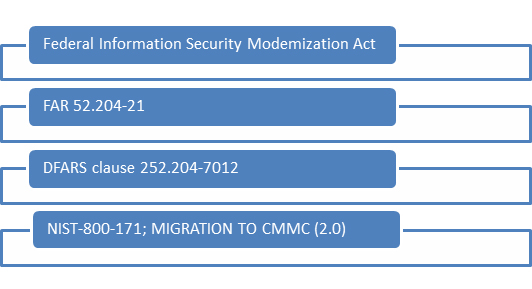
The Federal Information Security Modernization Act
The Federal Information Security Modernization (FISMA) Act of 2014 was enacted to modernize the federal governments cybersecurity practices. The main goal of FISMA is to:
- Codify Department of Homeland Security (DHS) authority to administer the implementation of information security policies for non-national security federal Executive Branch systems, including providing technical assistance and deploying technologies to such systems.
- Amend and clarifying the Office of Management and Budget's (OMB) oversight authority over federal agency information security practices.
- Require OMB to amend or revise OMB A-130 to eliminate inefficient and wasteful reporting.
FAR 52.204-21—Basic Safeguarding of Covered Contractor Information Systems
This is the Basic Safeguarding of Covered Contractor Information Systems. The main goal of FAR 52.204-21 is to have contractors follow crucial safeguarding requirements and procedures to protect covered contractor information systems.
Requirements and procedures for basic safeguarding of covered contractor information systems shall include, at a minimum, the following security controls:
- Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).
- Limit information system access to the types of transactions and functions that authorized users are permitted to execute.
- Verify and control/limit connections to and use of external information systems.
- Control information posted or processed on publicly accessible information systems.
- Identify information system users, processes acting on behalf of users, or devices.
- Authenticate (or verify) the identities of those users, processes, or devices, as a prerequisite to allowing access to organizational information systems.
- Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse.
- Limit physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals.
- Escort visitors and monitor visitor activity; maintain audit logs of physical access; and control and manage physical access devices.
- Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of the information systems.
- Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks.
- Identify, report, and correct information and information system flaws in a timely manner.
- Provide protection from malicious code at appropriate locations within organizational information systems.
- Update malicious code protection mechanisms when new releases are available.
- Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed.
Defense Federal Acquisition Regulation Supplement (DFARS) Clause 252.204-7012
DFARS clause 252.204.7012 is rising as a very applicable form of cybersecurity requirement for federal contractors.
Established under Executive Order 13556, DFARS 252.204-7012 requires contractors and subcontractors to:
- Provide adequate security to safeguard covered defense information that resides on or is transiting through a contractors internal information system or network.
- Report cyber incidents that affect a covered contractor information system or the covered defense information residing therein, or that affect the contractors ability to perform requirements designated as operationally critical support.
- Submit malicious software discovered and isolated in connection with a reported cyber incident to the DoD Cyber Crime Center.
- If requested, submit media and additional information to support damage assessment
- Flow down the clause in subcontracts for operationally critical support, or for which subcontract performance will involve covered defense information.
NIST 800-171 and the Migration to CMMC 2.0
NIST 800-171 refers to National Institute of Standards and Technology Special Publication 800-171, which governs Controlled Unclassified Information (CUI) in Non-Federal Information Systems and Organizations. NIST 800-171 requires contractors to protect controlled unclassified information in nonfederal systems and organizations. For more information on NIST 800-171, please visit the following NIST Special Publication SP 800-171.
It's important to note that the current NIST framework was used to create the building blocks for the Cybersecurity Maturity Model Certification (CMMC). CMMC, which is now CMMC 2.0, serves as an extension of DFARS 252.204-7012 by adding the certification process as verification for meeting FAR cybersecurity requirements.
Depending on the nature of the business your organization may be seeking, agencies or Contracting Officers may require this a certain level of CMMC prior to awarding a contract. Right now, CMMC is aimed at businesses in the Defense Industrial Base (DIB), but several solicitations and contract vehicles may be requiring it in the future. However, the official guidance is still in the works. More information on CMMC, and the process for attaining certification can be found on the Cyber AB site and the Acquisition and Sustainment webpage on CMMC FAQs.
Levels of cyber compliance to protect security information:
- The first level does its best to uphold any federal contract information.
- Then, the second level becomes a switch step in the cyber security maturity progression process, which then evolves into defense for proscribed, unclassified information (CUI).
- The third stage is to defend CUI.
- Finally, the fourth and final levels take into account protecting CUI and reducing the risk of advanced threats.
Importance of Cyber Compliance:
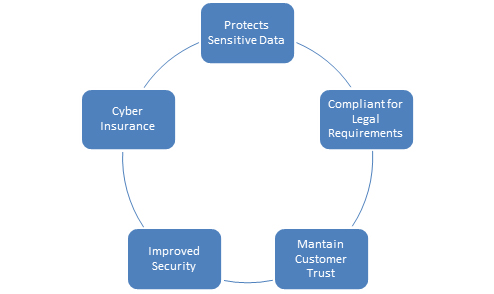
Figure 2
- Protects Sensitive Data: Compliance with rules and standards helps to make sure that an organization is taking the necessary steps to look after sensitive information, such as personal data and financial information. This helps to prevent data breaches, which can effect in significant financial losses and harm to an organization's reputation.
- Compliant for Legal Requirements: Failing to comply with regulations and standards can end up in significant fines and penalties, as well as legal actions. Compliance is essential to avoid these risks and ensure compliance with laws and regulations.
- Maintains Customer Trust: Compliance with regulations and standards can demonstrate to clients and partners that an organization takes data security and privacy seriously, that helps to build trust and maintain positive relationships.
- Improved Overall Security Posture: The process of achieving and maintaining compliance can also assist to advance an organization's overall security posture. This includes identifying and addressing vulnerabilities, implementing best practices, and frequently assessing and testing security controls.
- Obtaining Cyber Insurance: Many companies have cyber insurance that requires compliance with some standards and regulations. Non-compliance can end up in denial of claims and can make companies more vulnerable to a cyber attack.